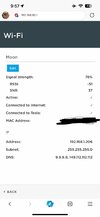
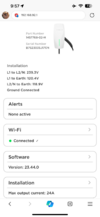
My Wall connector started showing "Offline" when I changed my firewall from IPFire to a Unifi gateway (UXG-Lite). I went back and forth with the Wall Connector support group and eventually they decided to send me a replacement charger even though I was 99.44% certain it was simply a "network" thing. Problem was, Tesla could SEE my TWC connected to their server(s) but it was still reporting "offline" in the app. (And that means no logging of charging history, etc.) The one question I never could get answered was what host FQDNs are requested by the TWC in making that connection to the AWS servers. Since Tesla thought it was connected, I'm beginning to believe the problem lies on HOW the connections are made the the servers.
After the new unit arrived and was installed, I continued to have the same "Offline" status so I decided to revert back to IPFire for a few days to see if the problem would go away and of course, it did. So, for now, I see some IP addresses that have been used by the TWC but I'm sure there must be a large POOL of IPs from AWS that are used. One IP/circuit seems to be possibly used for "Command and Control" while the other is used for exchanging much more data -- after a week, it's about 20MB on the data circuit and less than 1MB on the "C/C" circuit. I don't believe my IPFire provides an easy way for me to log DNS requests (and ideally, filter it from the TWC only) but I was hoping someone else out there has this ability and can monitoring these DNS requests to see what is being asked. Mostly, I think you'll see the requests within the first five minutes after it's powered on and it's established its connection to wireless. Once that happens, it seems to make three connections but terminates one of them very quickly--perhaps to first connect with an authentication server to find the owner's Tesla account and establish the necessary info to make the Command/Control circuit. After that the "data exchange" circuit seems to get established. But I'm seeing different IP almost each time.
Ultimately I am trying to figure out how to get it working under my Unifi Gateway, so perhaps another question is for anyone using a Unifi infrastructure at home that also has a TWC and has figured out how to make it appear "online" in the app.
Thanks!
After the new unit arrived and was installed, I continued to have the same "Offline" status so I decided to revert back to IPFire for a few days to see if the problem would go away and of course, it did. So, for now, I see some IP addresses that have been used by the TWC but I'm sure there must be a large POOL of IPs from AWS that are used. One IP/circuit seems to be possibly used for "Command and Control" while the other is used for exchanging much more data -- after a week, it's about 20MB on the data circuit and less than 1MB on the "C/C" circuit. I don't believe my IPFire provides an easy way for me to log DNS requests (and ideally, filter it from the TWC only) but I was hoping someone else out there has this ability and can monitoring these DNS requests to see what is being asked. Mostly, I think you'll see the requests within the first five minutes after it's powered on and it's established its connection to wireless. Once that happens, it seems to make three connections but terminates one of them very quickly--perhaps to first connect with an authentication server to find the owner's Tesla account and establish the necessary info to make the Command/Control circuit. After that the "data exchange" circuit seems to get established. But I'm seeing different IP almost each time.
Ultimately I am trying to figure out how to get it working under my Unifi Gateway, so perhaps another question is for anyone using a Unifi infrastructure at home that also has a TWC and has figured out how to make it appear "online" in the app.
Thanks!